To understand stream ciphering, just remind for example those videos encoded with the
RealVideo format, widely known on the internet : one watches the pictures as soon as they
reach the computer; you don't have to wait for the whole file to be received. This principle applies
to our stream-ciphers : encryption is performed bit per bit without waiting for the
complete reception of the data to be encrypted. The result is a very light encryption that
doesn't ensure high confidentiality; indeed, the number of possibilities that offers a single
bit is very limited and that reduces the overall efficiency of the algorithm. If this one
was taking into account the previous or following bits, the number of possibilities would be
ten times greater as we will see in the study of the 4 modes.
Another technique consists to apply a logical XOR, that is to say to perform an exclusive OR
between the message and another predefined message. Of course, it requires both sides to know
this predefined message, thus increasing the overall complexity of the scheme. Stream ciphers
are not used a lot in today's applications (as we will see, block ciphers can even perform a
kind of stream ciphering now)
Block ciphering is a lot more used and allows a better security.
Its algorithms are also wellknown (DES, AES, Skipjack...); their name comes from the fact that
they operate on blocks of data instead of single bits (cf stream ciphers). Those blocks have
usually 64 bits but
this depends completely on the selected algorithm and on its implementation. In the same idea,
the size of the key can vary depending on the algorithm and the required level of security.
Thus, a 40-bits encryption (ie that uses a key size of 40 bits) is said to be weak because easily
breakable. A 56-bits encryption (which is the standard for DES) is average for it can be
broken but that requires some means in order to be valuable (in regards to the time needed and
the value of the data). Eventually, a 128-bits encryption (standard value for AES aka Rijndael)
is quite strong today.
At this subject, let's remind Moore's law about the processing power, which foresees that
figures will double every 18 months. Without going into details, one must know that breaking
ciphers essentially requires processing power and RAM. So, the general evolution is very fast
and it is difficult to talk about absolute security especially when dealing with symmetric
cryptography.
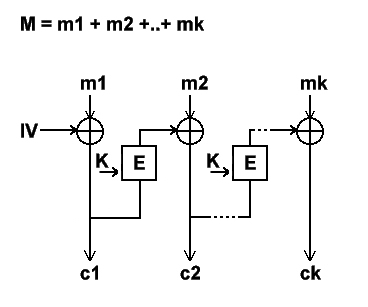
The 4 modes that have been introduced above are more or less independents from the algorithms.
However, not all algorithms support them. For a better understanding, let's see those
modes closer. In order to make the comprehension easier, we will use the following
notation :